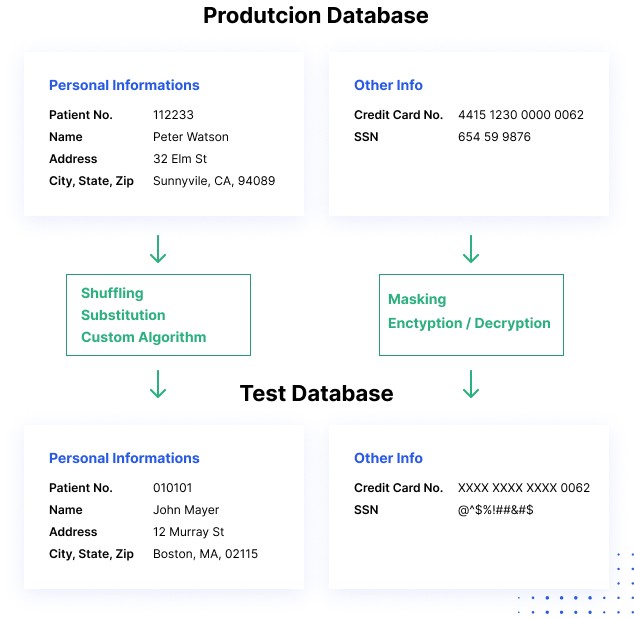
Data Masking Counter Attack to Identity Theft Paul Preston Data Masking: Counter Attack to Identity Theft. - ppt download

References in Montreal Accord on Patient-Reported Outcomes (PROs) use series – Paper 9: anonymization and ethics considerations for capturing and sharing patient reported outcomes - Journal of Clinical Epidemiology

Informatica Persistent Data Masking VS Informatica Dynamic Data Masking - compare differences & reviews?

Primer on GDPR Pseudonymization. Personal data is any information… | by Balaji Ramakrishnan | Medium

De-identification and re-identification of PII in large-scale datasets using Cloud DLP | Cloud Architecture Center | Google Cloud


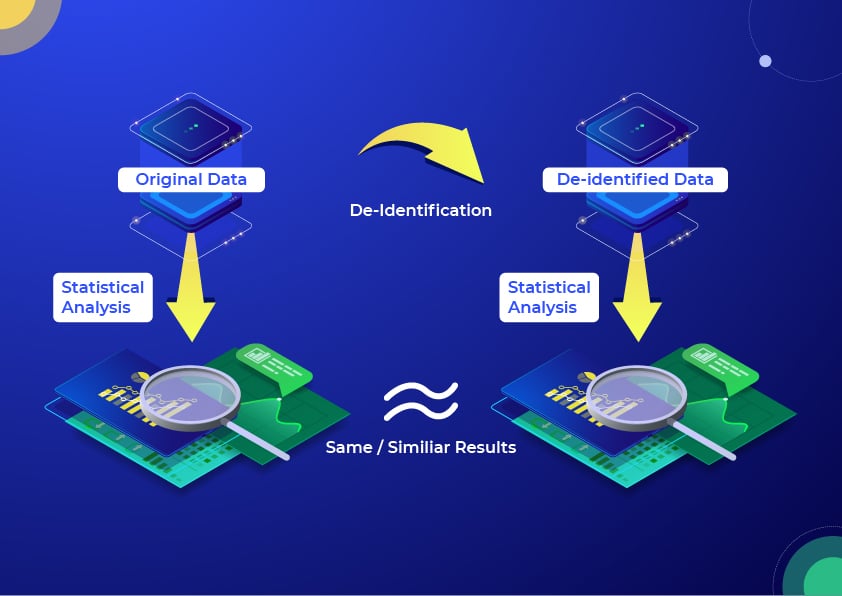

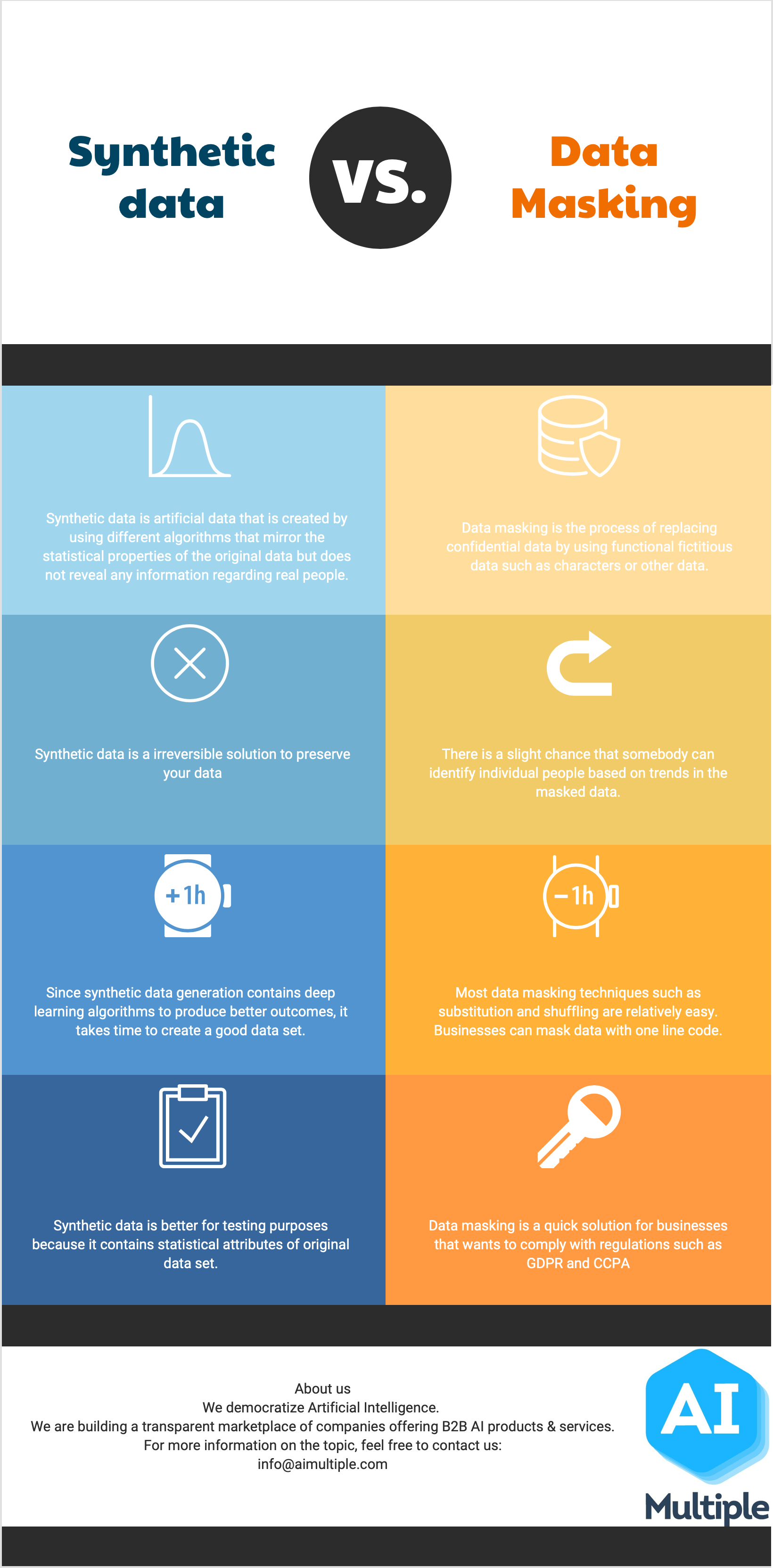

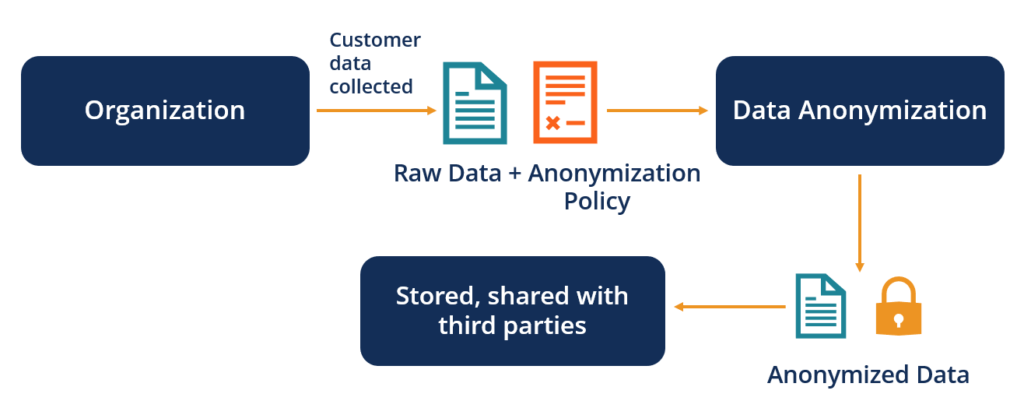


![1. Introduction - Anonymizing Health Data [Book] 1. Introduction - Anonymizing Health Data [Book]](https://www.oreilly.com/library/view/anonymizing-health-data/9781449363062/images/anhd_0101.png)

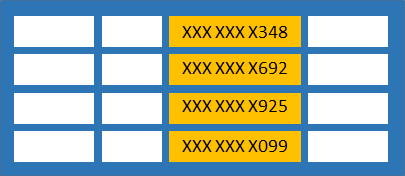
![Data Masking and Encryption Are Different [video] - IRI Data Masking and Encryption Are Different [video] - IRI](https://i.ytimg.com/vi/LuO7bi9uRh4/maxresdefault.jpg)