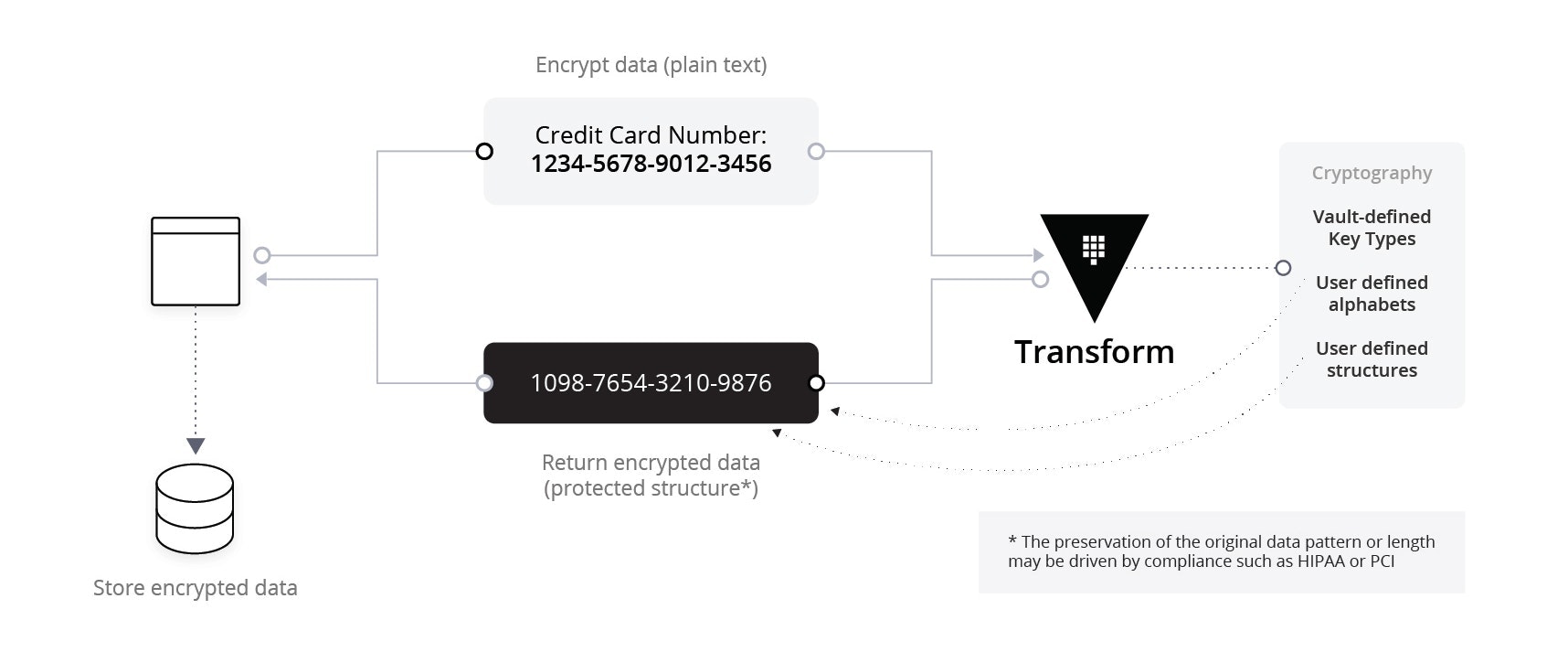
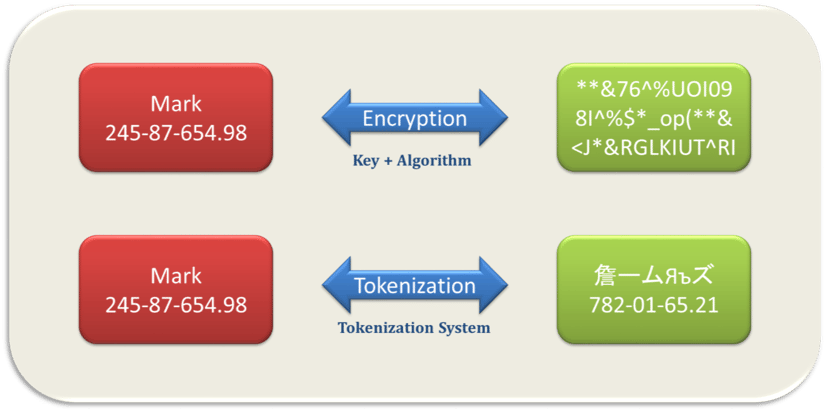
Data Masking: Difference between data encryption and data masking - opjuqzsdofbube vs da** ma***** - DevInline - Tech Blog
Data Masking Vs Encryption Ppt Powerpoint Presentation Gallery Graphics Download Cpb | PowerPoint Templates Download | PPT Background Template | Graphics Presentation
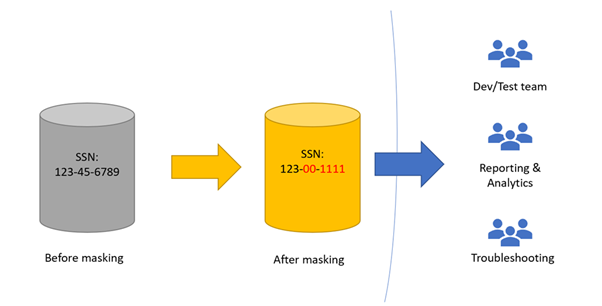
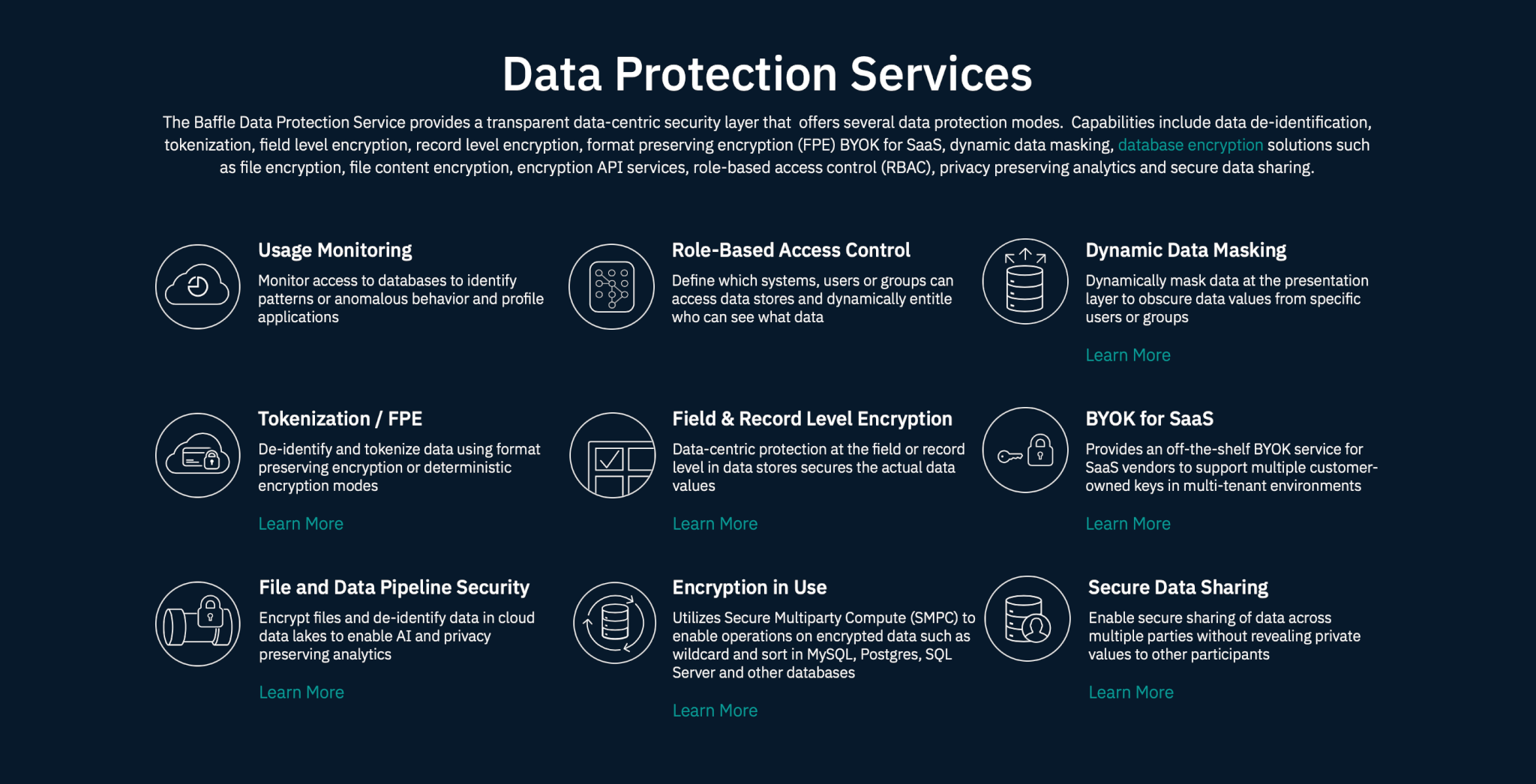
Data Masking : Concept, Tools, Masking polices & Healthcare Data Masking | by Samadhan Kadam | Petabytz | Medium


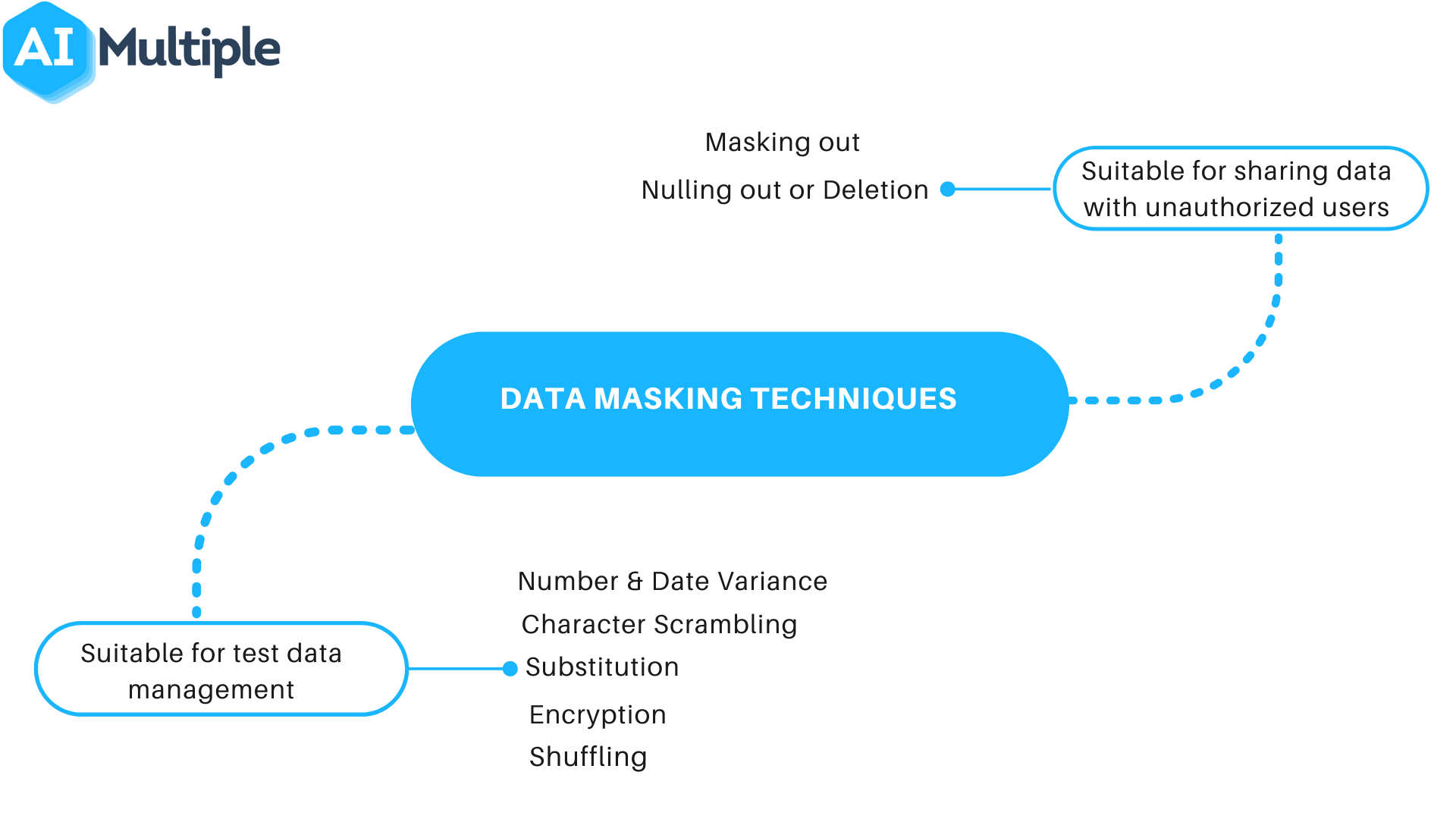

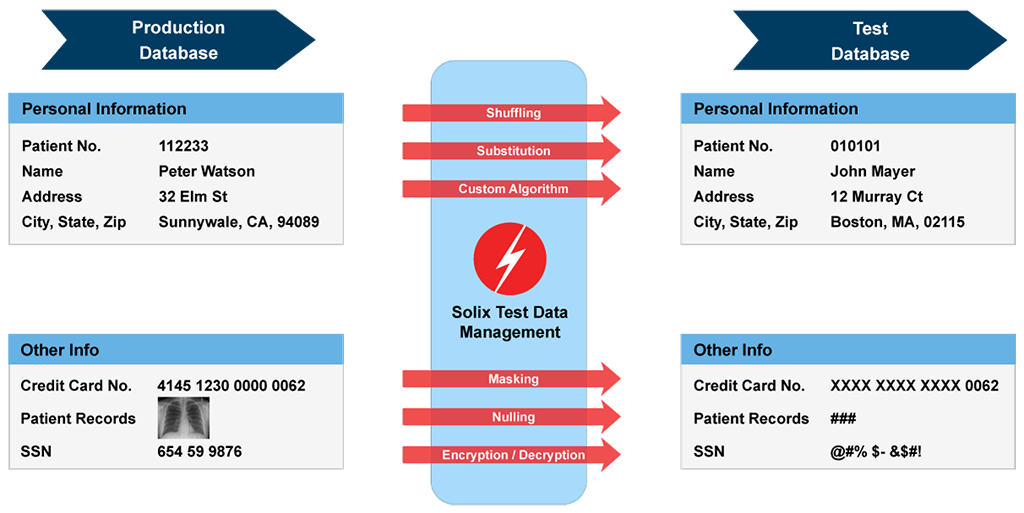



![Data Masking and Encryption Are Different [video] - IRI Data Masking and Encryption Are Different [video] - IRI](https://i.ytimg.com/vi/LuO7bi9uRh4/maxresdefault.jpg)